이 글은 내가 ECDSA 기반 TLS 1.2 와 DTLS 1.2 스펙을 구현 하면서 알게 된 내용이다.
그러다 보니 알게 된 메모글이라 수시로 업데이트 할 예정이다.
기존에 TLS 관련 지식은 다음 링크를 참조 하면 된다.
여기서는 단지 개발 하면서 파악된 내용을 간단히 기록 하였다.
만약에 TLS에 관한 기본 지식을 파악하고 싶으면 아래 링크를 참조 하세요.
TLS 에 관한 정보 링크
https://dokydoky.tistory.com/462
https://dokydoky.tistory.com/463
https://dokydoky.tistory.com/464
DTLS 특성
DTLS ( Datagram Transformt Layer ) 는 UDP 환경에서 TLS 전송을 하기 위한 프로토콜이다.
그리고 DTLS 1.0은 TLS 1.1 을 기반으로 만들어 졌구. DTLS 1.2 는 TLS 1.2 기반으로 만들어 졌다.
DTLS 1.2 표준 스펙은 [RFC6347] 을 참조 하면 된다.
TLS 1.2 표준스펙은 [RFC5246] 을 참조 하면 된다.
ECC CipherSuite [RFC4492] 표준 스펙
참고로 공개키 기반 구조로 DTLS 를 구현한 오픈소스 사이트는 아래를 참조 하면된다.
[TinyDTLS] 참고로 이 사이트는 나도 Github 에서 포크해서 가져온 소스이다.
DTLS에서는 HelloVerifyRequest 부분이 존재 하구
TLS에서는 이 과정은 존재 하지 않는다.
DTLS에서는 전송에 대한 보장이 없기 때문에 패킷에 대한 sequence 와 epoch 값을 사용하여 해당 패킷의 재전송을 통한
값에 확인 하는 부분이 존재한다.
DTLS 패킷 프레임을 보면
Type(1) | Version(2) | Epoch(2) | Sequence Number(6) | Length(3) | ...
TLS 패킷 프레임은
Type(1) | Version(2) | Length(3) | ...
이렇게 epoch 와 sequence number 값의 유무가 차이 난다.
epoch 값은 DTLS에서만 사용하는 값으로 Cipher 상태가 변화가 일어 날때 마다 1씩 증가 하는 값이다.
TLS 특성
TLS 프로토콜은 상호인증 및 단방향 인증 두가지가 지원 된다.
단방향 인증이야 상호 인증이냐는 서버 쪽에서 결정 한다.
단방향 인증에서는 CertificateRequest랑 Client Certificate, CertificateVerify 가 없음
대칭키 알고리즘의 키 길이를 256 비트를 사용 하게 되면 SHA-2 알고리즘 경우 SHA-384 만 가능하다.
키 길이 128 비트인 경우는 SHA-256 비트의 무결성 알고리즘을 사용한다.
ECDH 와 ECDHE 차이점
ECDH 를 사용 할 경우 서버 인증서에서 KeyUsage 필드에 Key Agreement 가 필요 함
ECDH 를 하게 되면 ServerKeyExchange 메세지는 보내지 않음 하지만 ClientKeyExchange 는 보냄
HandShake 과정
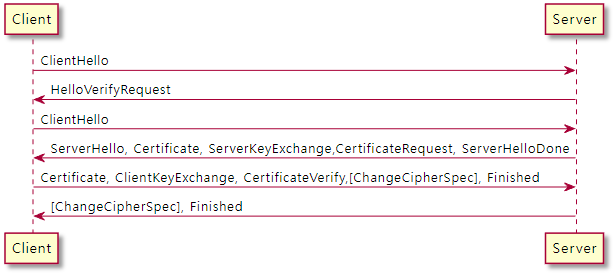
DTLS 1.2 상호 인증
TLS 1.2 상호 인증

TLS 1.2 서버 인증
일반적으로 HTTPS 주소로 접근시 서버 인증 방식을 사용한다.
서버 인증인 경우 클라이언트에서는 특별히 인증서를 사용하지 않는 방식이다.

ClientHello
클라이언트에서 처음 TLS 시작을 알리는 메제지 이다.
사용하는 알고리즘 알려줌
struct {
uint32 gmt_unix_time;
opaque random_bytes[28];
} Random;HelloVerifyRequest
서버에서 쿠키 값을 알려줌 DTLS는 연결을 보장 하지 않다 보니 연결에 대한 구별 값
DTLS에서만 사용 함
struct {
ProtocolVersion server_version;
opaque cookie<0..2^8-1>;
} HelloVerifyRequest;ServerHello
서버에서 허가 한 알고리즘 이랑 Random 값 알려줌
struct {
ProtocolVersion server_version;
Random random;
SessionID session_id;
CipherSuite cipher_suite;
CompressionMethod compression_method;
select (extensions_present) {
case false:
struct {};
case true:
Extension extensions<0..2^16-1>;
};
} ServerHello;Certificate
서버 또는 클라이언트에서 사용하는 인증서 값을 보내줌
클라이언트에서는 서버가 CertificateRequest를 보내야만 클라이언트에서는 전송 함
서버 경우 인증서 체인으로 전달 함. 첫번째가 실제 서명용 인증서 임
opaque ASN.1Cert<1..2^24-1>;
struct {
ASN.1Cert certificate_list<0..2^24-1>;
} Certificate;ServerKeyExchange
pre master secret 생성을 위한 파라미터 정보를 보내줌
struct {
select (KeyExchangeAlgorithm) {
case dh_anon:
ServerDHParams params;
case dhe_dss:
case dhe_rsa:
ServerDHParams params;
digitally-signed struct {
opaque client_random[32];
opaque server_random[32];
ServerDHParams params;
} signed_params;
case rsa:
case dh_dss:
case dh_rsa:
struct {} ;
/* message is omitted for rsa, dh_dss, and dh_rsa */
/* may be extended, e.g., for ECDH -- see [TLSECC] */
};
} ServerKeyExchange;CertificateRequest
클라이언트 인증서 요청 하는 경우 보냄
struct {
ClientCertificateType certificate_types<1..2^8-1>;
SignatureAndHashAlgorithm
supported_signature_algorithms<2^16-1>;
DistinguishedName certificate_authorities<0..2^16-1>;
} CertificateRequest;ServerHelloDone
서버에서 메세지를 다 보냈다구 알려줌
struct { } ServerHelloDone;ClientKeyExchange
클라이언트 보안 파라미터를 보내줌
struct {
select (KeyExchangeAlgorithm) {
case rsa:
EncryptedPreMasterSecret;
case dhe_dss:
case dhe_rsa:
case dh_dss:
case dh_rsa:
case dh_anon:
ClientDiffieHellmanPublic;
} exchange_keys;
} ClientKeyExchangeCertificateVerify
현재 까지 보낸 메세지의 해쉬값에 대한 전자 서명을 보냄
지금 까지 보낸 Handshake의 모든 메세지에 대한 서명 값을 넣어서 보냄.
struct {
digitally-signed struct {
opaque handshake_messages[handshake_messages_length];
}
} CertificateVerify;ChangeCipherSpec
성공적 키 공유 했음과 이후 메세지는 암호화 임을 알림
struct {
enum { change_cipher_spec(1), (255) } type;
} ChangeCipherSpec;Finished
핸드쉐이크의 성공을 암호화로 알림
지금 까지 모든 Handshake 메세지에 대한 Hash 값을 포함 하여 전달
struct {
opaque verify_data[verify_data_length];
} Finished;이렇게 Handshake 가 끝나고 나면 ApplicationData 전송을 통한 데이타 전송이 이루어 진다.
이때 ApplicationData 경우도 Sequence 번호를 사용하여 순서에 대한 보장이 이루어 저야 한다.
'PKI > TLS' 카테고리의 다른 글
| SSL 인증서와 https 도메인 주소 연관성 (0) | 2023.06.08 |
|---|---|
| TLS 핸드쉐이크 기능 간단 설명 (0) | 2023.06.08 |
| TLS 에서 ECDH 키 합의 경우 PRF (PseudoRandom Function) 방식 (0) | 2023.04.14 |