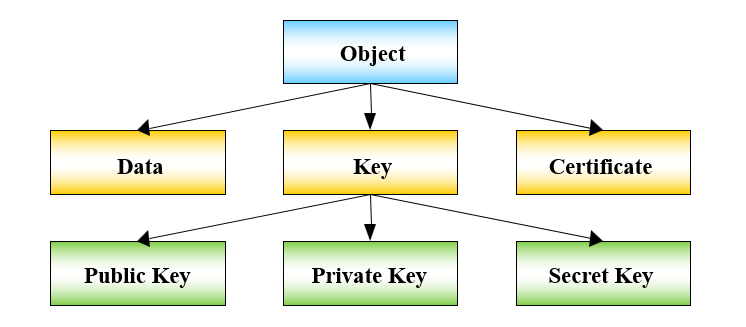
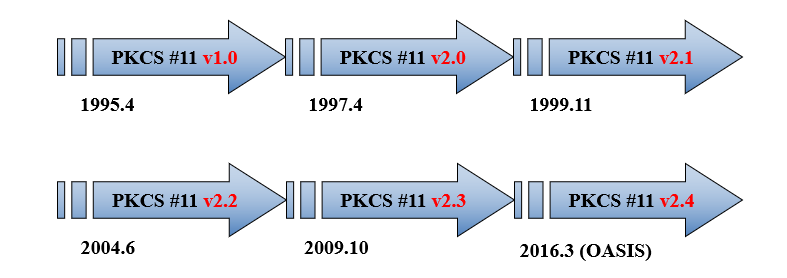
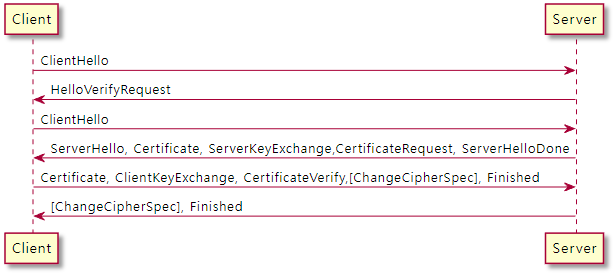
OpenSSL 은 0.9.xx 에서 그리고 1.1.1x 버전에서 3.0 버전(출시일: 2021-09-07) 으로 나왔다. 현재 3.0 버전에서는 FIPS모듈의 사용과 새로운 기능을 활용해야 하는 경우 3.0 으로 변경을 해야 한다. 글을 쓰는 이 시점에는 3.1 버전 (출시일: 2023-03-14) 까지 나와 있다. 그럼 주요 변경 사항에 대해 알아 보자. 이 글은 OpenSSL 3.0 위키를 참조 하였다. 1. 라이센스 변경 - 기존 openssl 은 OpenSSL 과 SSLeay 라이센스에서 Apache License v2 로 변경 되었다. 이 부분은 GPL 라이센스와의 문제를 해결하기 위해 변경 되었다. 2. FIPS 인증 모듈 포함 - Openssl 1.1.1 에서는 FIPS 모듈을 따로 패키지 ..